We’ve already seen how to restrict software on Windows Server 2012 // R2 using GPOs. There’s another way available since Windows Server 2012, thanks to a feature called AppLocker.
We still use GPOs – AppLocker is a subset of GPOs – to enforce software restriction but it’s easier and more powerful.
AppLocker can manage execution permissions of:
- Executables: files with .exe extension
- Windows installers: Windows installer packages with .msi and .msp extensions
- Scripts: files with .ps1, .bat, .cmd, .cbs and .js extensions
- Packaged Apps: Windows Store apps
Open the Server Manager and launch the Group Policy Management:
Create a new GPO:
Edit the policy:
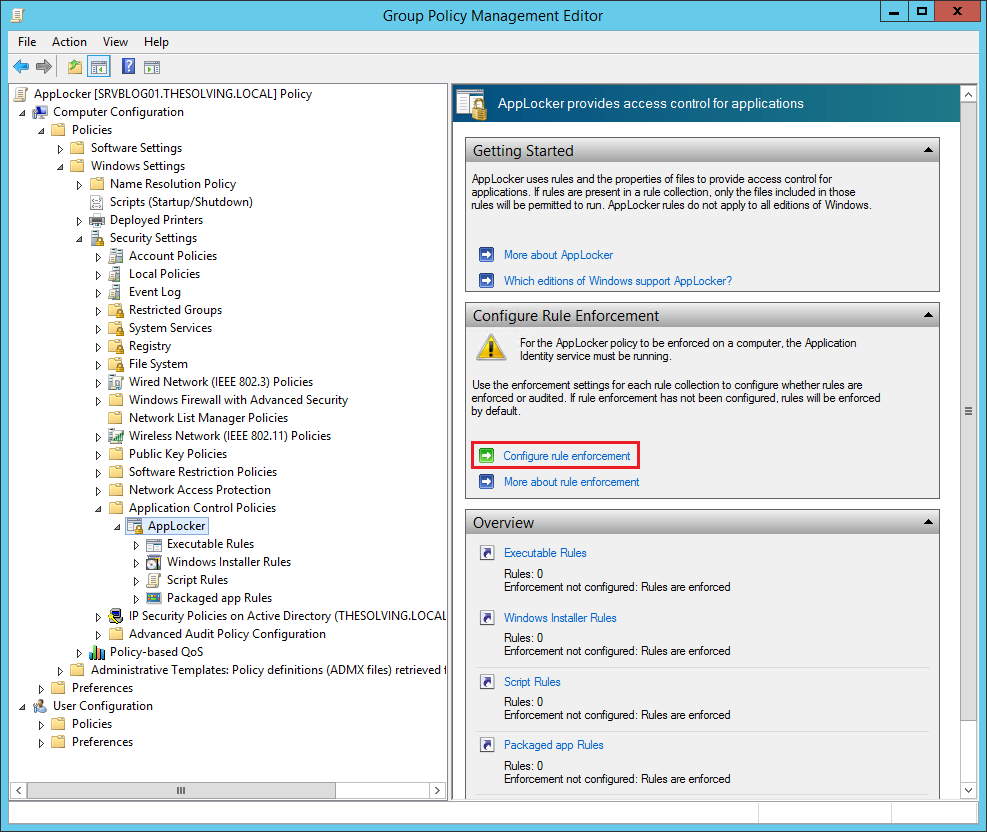
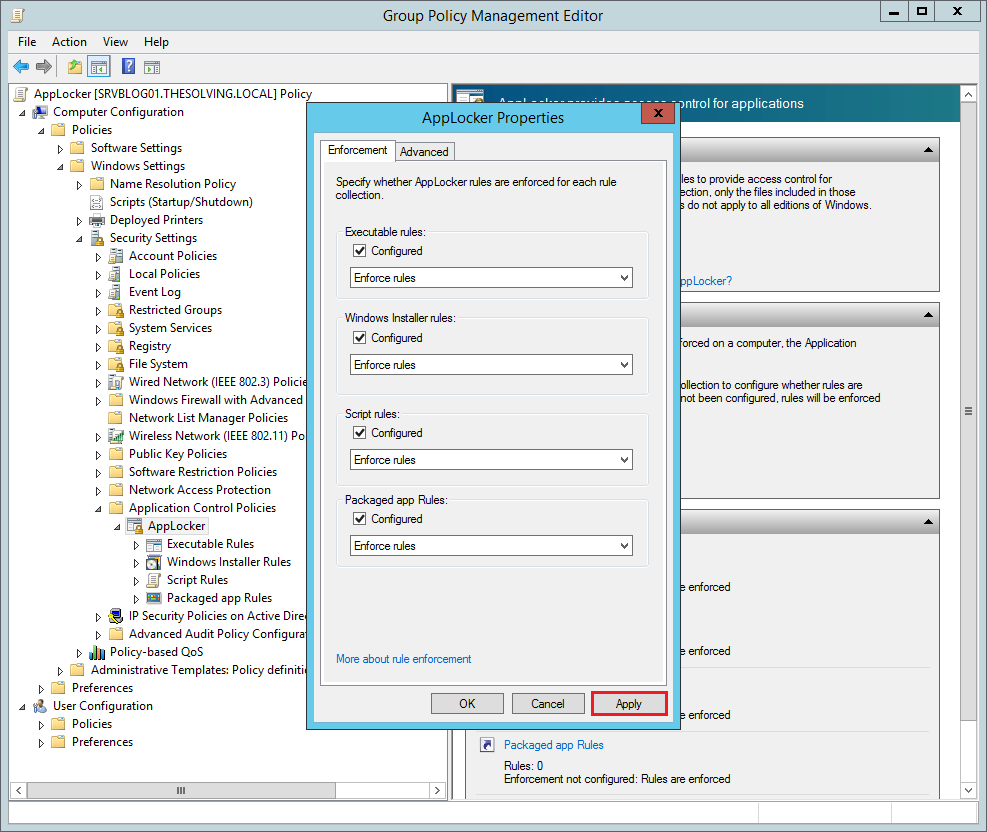
You will find the AppLocker settings inside the path Computer Configuration\Policies\Windows Settings\Security Settings\Application Control Policies\AppLocker. Click Configure rule enforcement:
Check all the rules if you want to enforce them. By default AppLocker blocks all executables, installer packages and scripts, except for those specified in Allow rules:
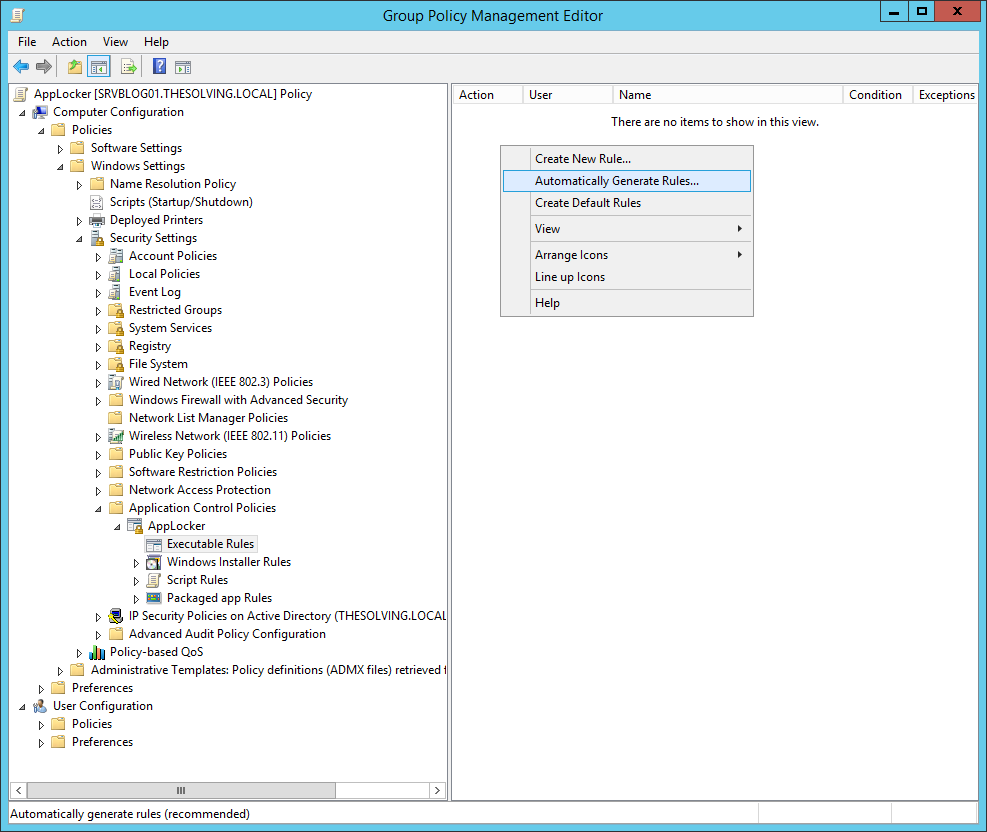
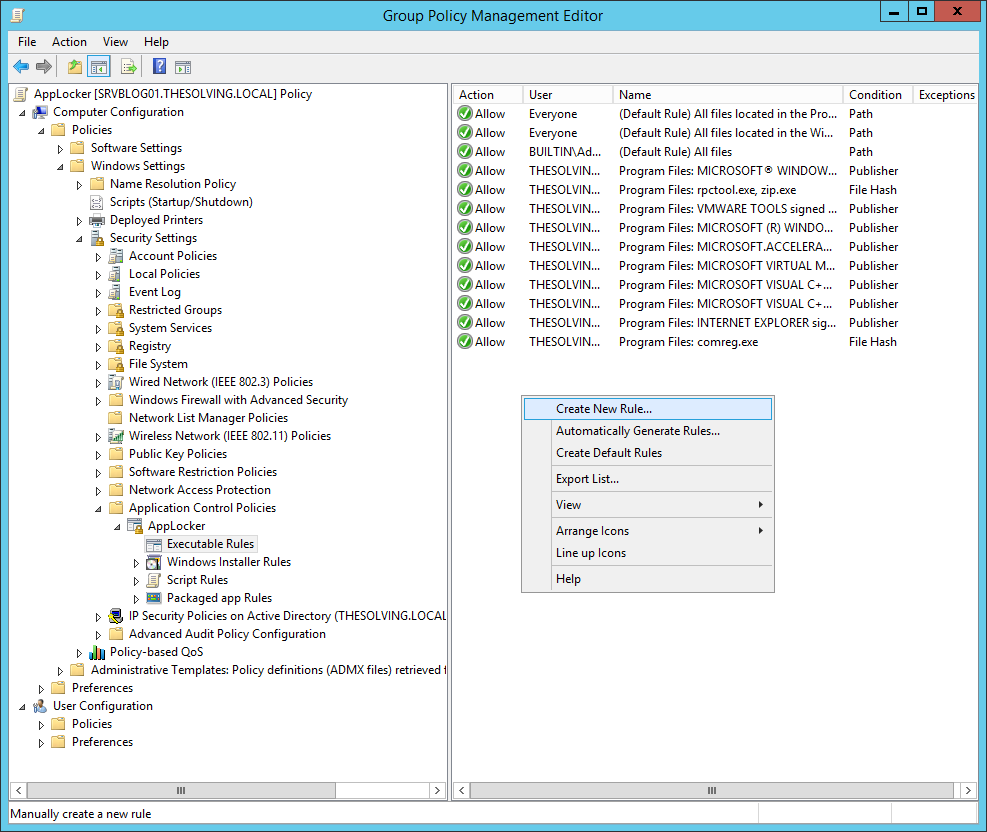
AppLocker differs from software restriction policies for the ability to automatically create rules. Right-click in the white box and select Automatically Generate Rules, a wizard will appear:
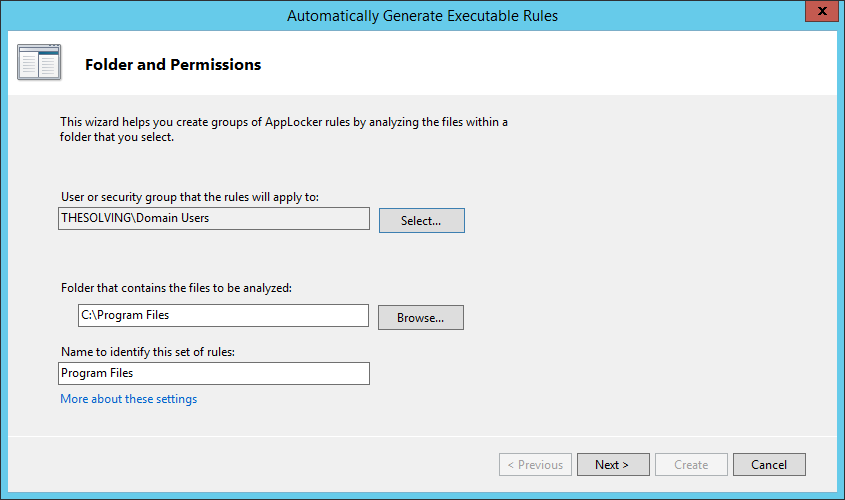
Specify the users that will be affected and select the path that will be analyzed to automatically create “Allow execute” rules:
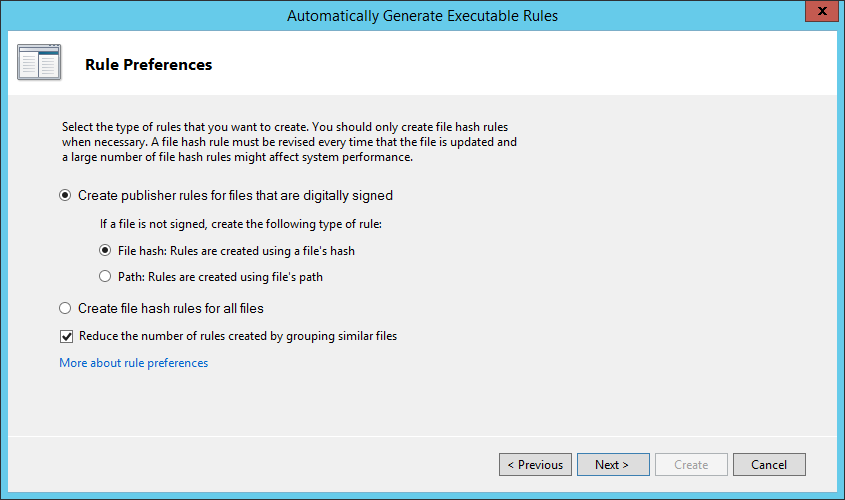
You can choose to allow or not-allow the execution of unsigned executables. It’s better to create the rules based on the executable hash rather than the file path, it’s more reliable:
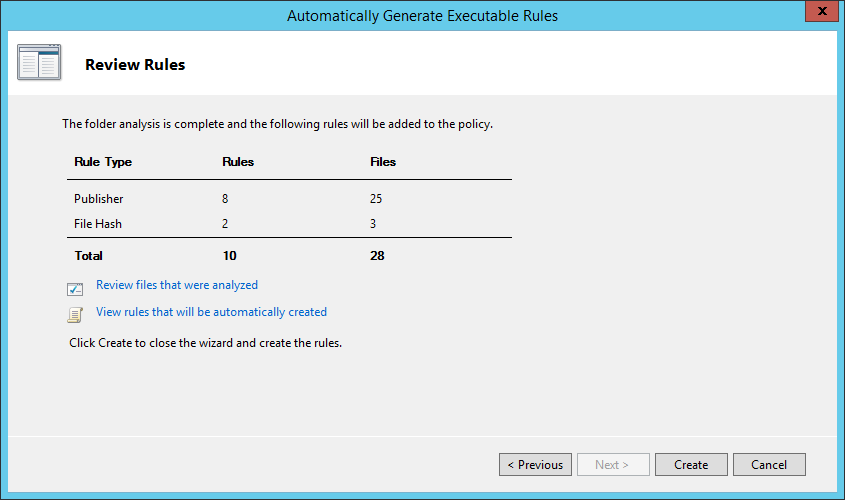
Click Create:
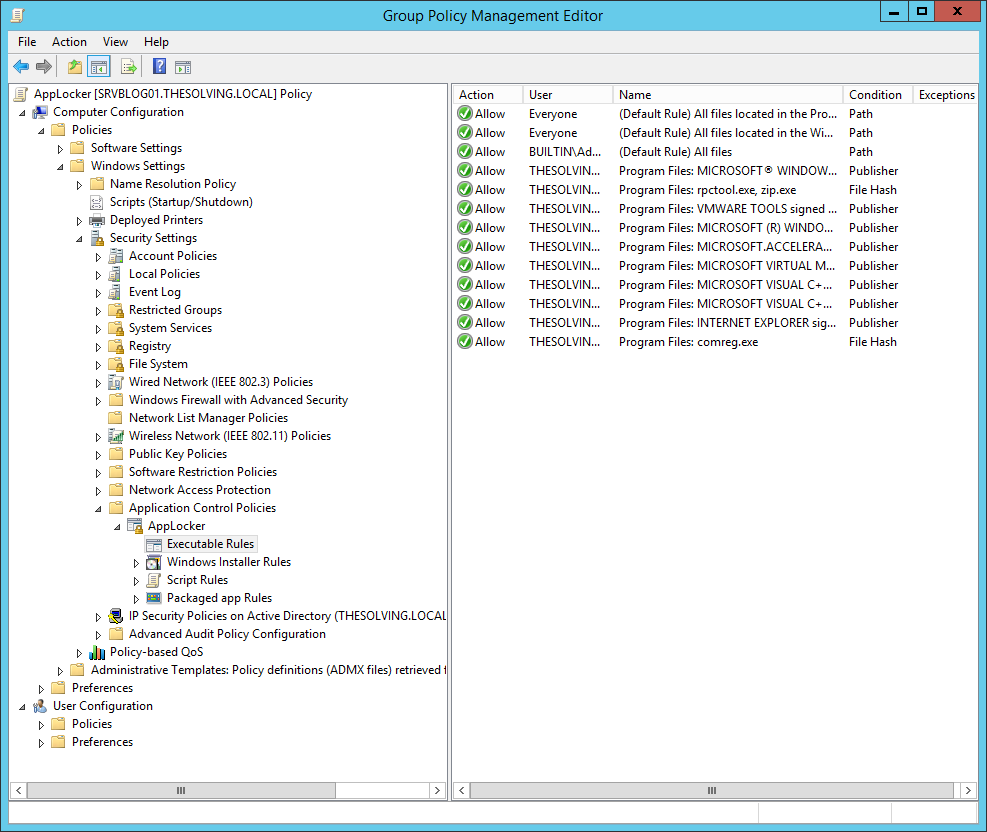
The new rules will appear:
We can also manually create other rules. Right-click on the background and choose Create New Rule:
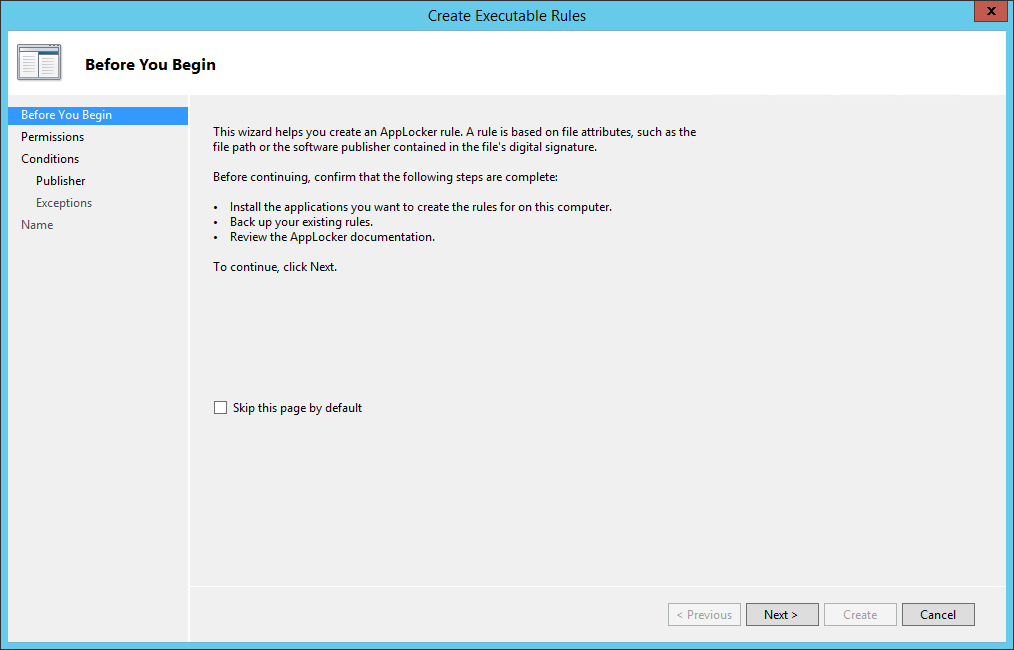
Click Next:
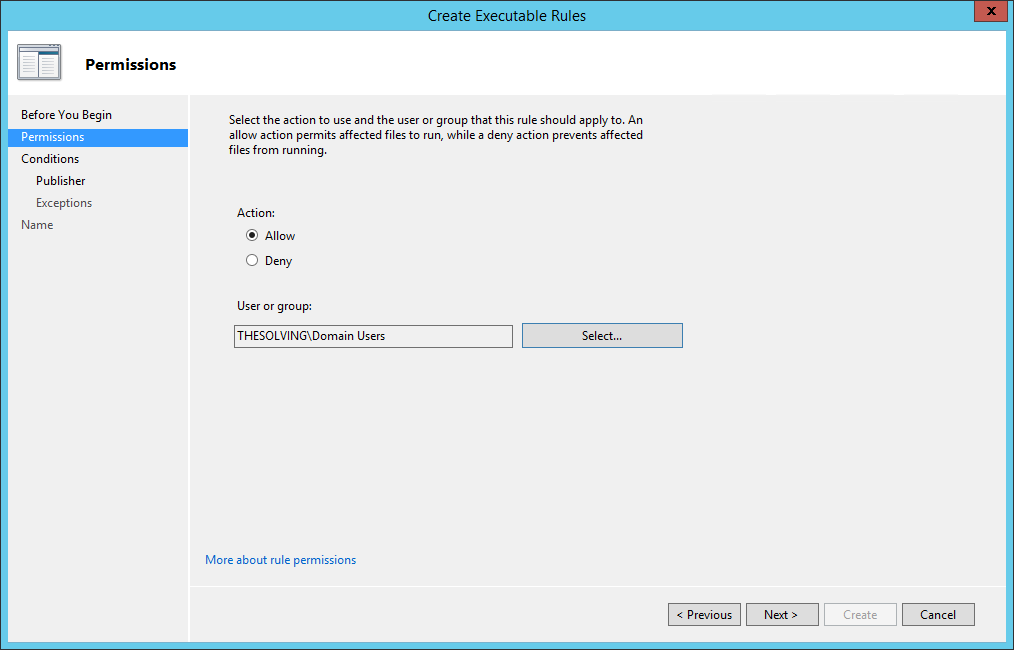
Specify the users who will be affected by the rule and the rule type (Allow or Deny execution):
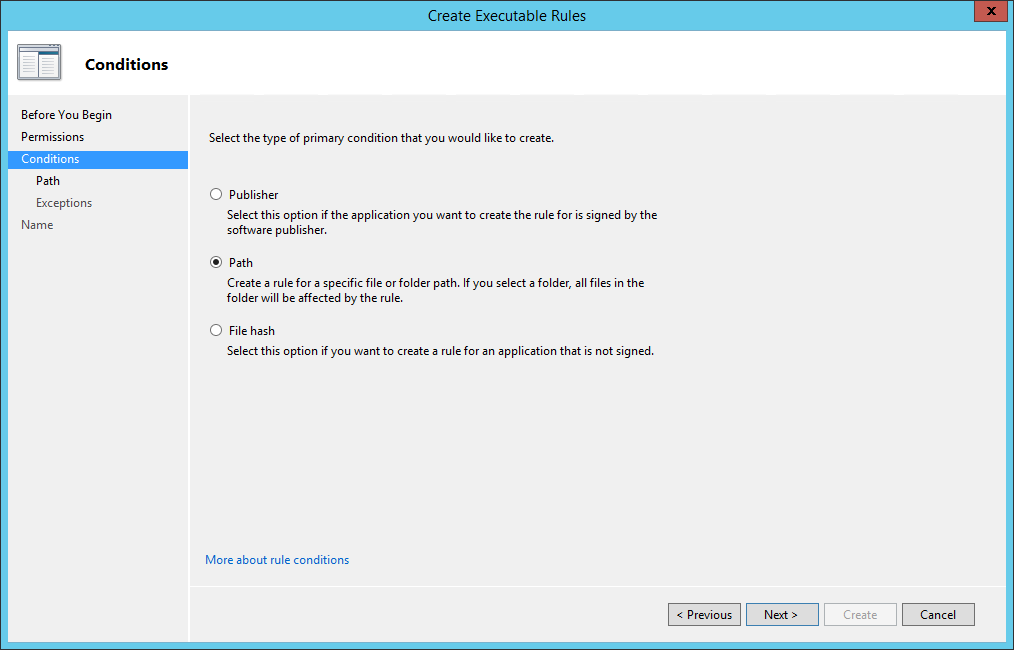
There are three ways to specify which applications will be affected by the rule:
- Publisher: identify the applications signed by a specific publisher;
- Path: identify specific files and paths;
- File Hash: identifiy applications based on their digital fingerprint.
In our example we chose Path:
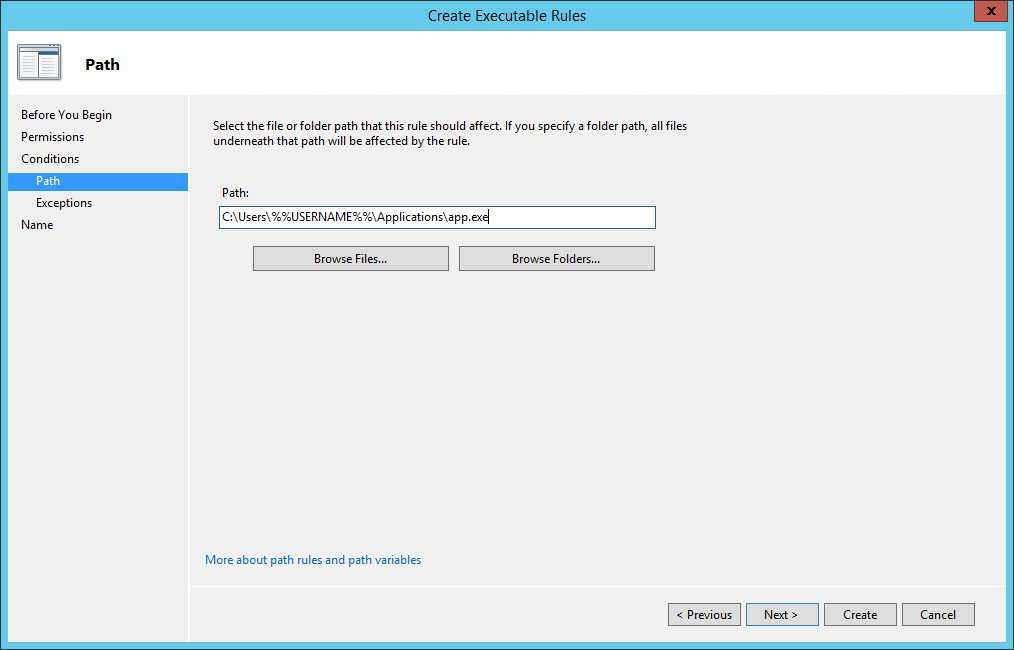
Specify the Path:
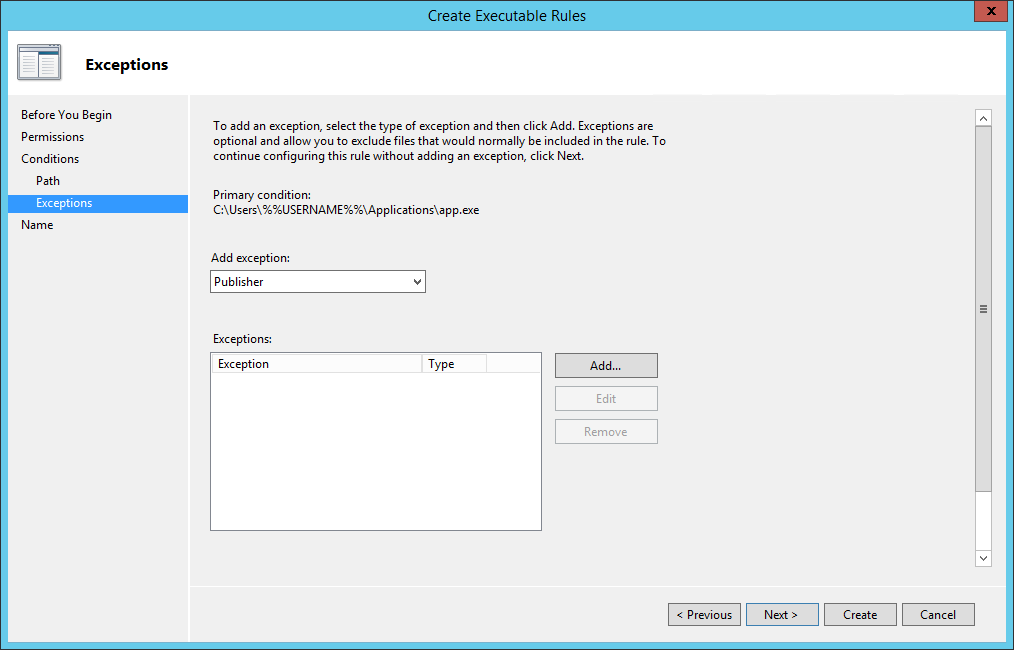
You can add exceptions if you need them:
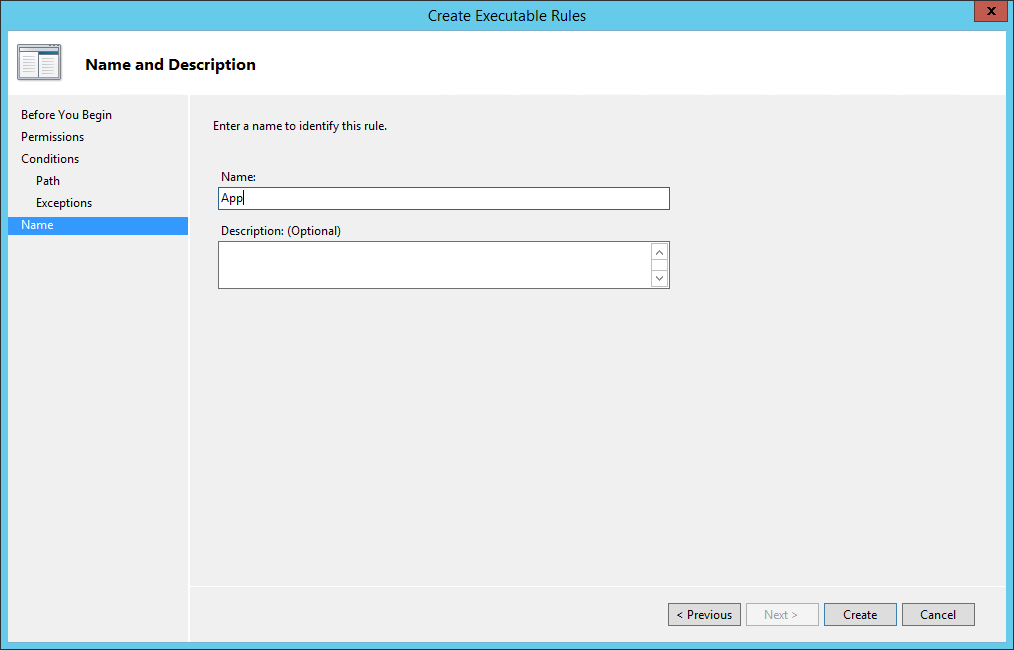
Name your new rule and click Create:
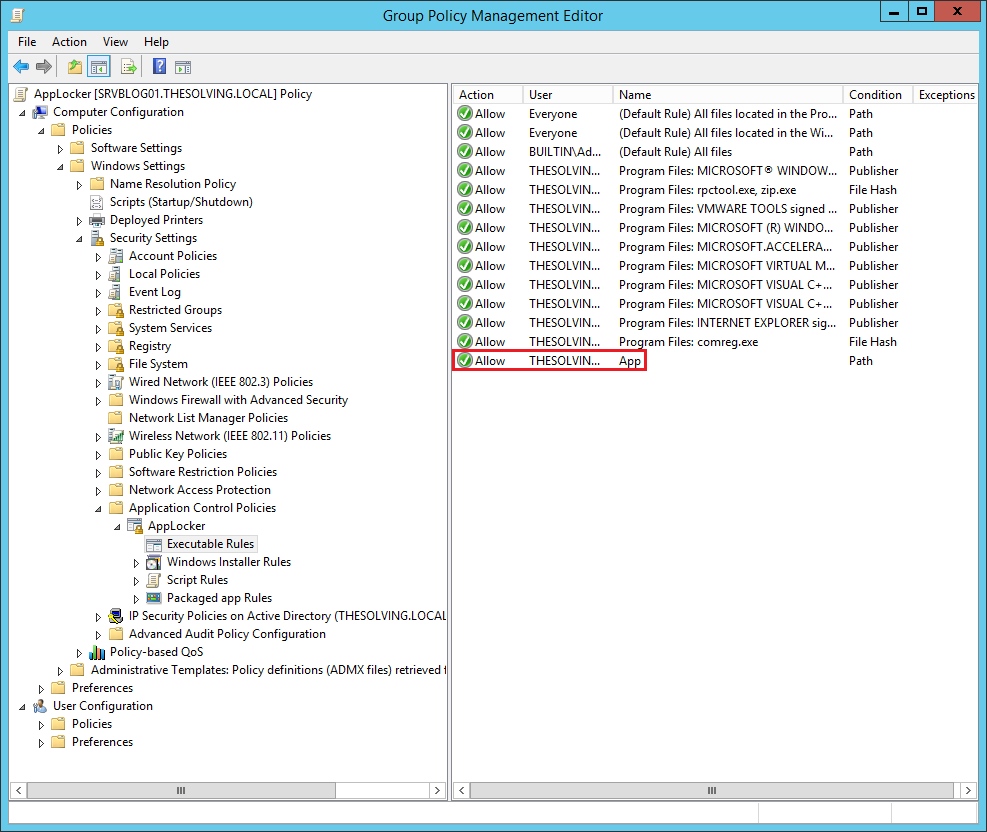
The rule will appear:
Read related articles
A Guide to PowerShell – part 3
Welcome to part 3 of 3 of The Solving A guide to PowerShell. Check also Part 1 and Part 2.
A Guide to PowerShell – part 2
Welcome to part 2 of 3 of The Solving A guide to PowerShell. Click here for Part 1 and Part
A Guide to PowerShell – part 1
Welcome to part 1 of 3 of The Solving A guide to PowerShell. Click here for Part 2 and Part

 Italiano
Italiano
 Español
Español